Cybersecurity
Information is Money
Your data is valuable, which means that it is always at risk. Hackers are constantly and methodically attempting to compromise your system's security for their financial gain. Many businesses are unable to recover from a massive data breach.
According to a 2022 study by the Ponemon Institute, the average cost of a data breach in the United States is $9.44 million. This figure includes direct costs, such as legal expenses and notification costs, as well as indirect costs, such as lost business and damage to an organization’s reputation.
$9.44 MILLION
Average Cost of a Data Breach
Let's Get to Work
Common Threats
Malware
Software that is designed to damage or disrupt computer systems. Examples include viruses, worms, and trojans.
Top 3 Dangers of Malware:
- Data Loss
- System Disruption
- Network Compromise
Ransomware
Type of malware that encrypts a victim's data and demands a ransom from the victim to restore access. Countless businesses have been forced to pay a ransom to restore access to their data, which can be expensive and may not guarantee the safe return of the data.
Top 3 dangers of ransomware:
- Financial Loss
- Data Loss
- Reputational damage
Phishing
A type of social engineering attack that involves sending fraudulent emails or messages in an attempt to trick the recipient into revealing sensitive information, such as login credentials or financial information.
Top 3 dangers of phishing:
- Not detectable by normal malware scanning tools.
- Loss of personal or company information.
- Introduction of malware via a backdoor.
MITM Attacks
A type of attack in which the attacker intercepts and modifies communication between two parties without their knowledge. Communications can be manipulated in order to commit fraud, such as altering financial transactions or impersonating a legitimate party.
Top 3 dangers of Man-in-the-Middle attacks:
- Attackers could alter an account number or amount being sent in a financial transaction.
- Forced compromises could install malware.
- Unsecured IoT devices could send false information back to the organization.
Zero-day Vulnerabilities
Type of cyber attack that exploits a previously unknown vulnerability in software or hardware. These vulnerabilities are often discovered by attackers and exploited before the manufacturer has had a chance to release a patch to fix the issue.
Top 3 dangers of zero-day vulnerabilities:
- Attack method has not been seen before and may not have a defense.
- If layered defenses aren’t in place, attack could be extremely disruptive.
- Older technology can be particularly susceptible.
Insider Threats
The risk of malicious or unintentional actions by employees, contractors, or other insiders that can compromise the security of a business. These threats can come in the form of sabotage, theft, or accidental data breaches.
Top 3 dangers of insider threats:
- Could be a sign of poorly educated employees.
- Inside employees have access to sensitive company data.
- Can be difficult to detect.
The Potential Risk
Education
Education institutions are a major target for data breaches due to the large amount of personal data they maintain including student/family information and faculty records.
Financial Services
The financial services industry is a prime target for cyber criminals who want to access bank account information and credit card numbers for financial gain.
Healthcare
Health care providers are often targeted by cyber criminals because they maintain sensitive data like patient medical records and insurance information.
Legal
Law firms require clients to provide confidential documents as part of the legal process, including personal data, financial information, and healthcare records.
Manufacturing
The manufacturing industry handles highly sensitive and confidential information, such as product designs, intellectual property, and customer data.
Local Government
Local Governments maintain sensitive and confidential information, such as personal data, property ownership & tax documents, financial information, and other proprietary data.
Synergy's Protection Strategy
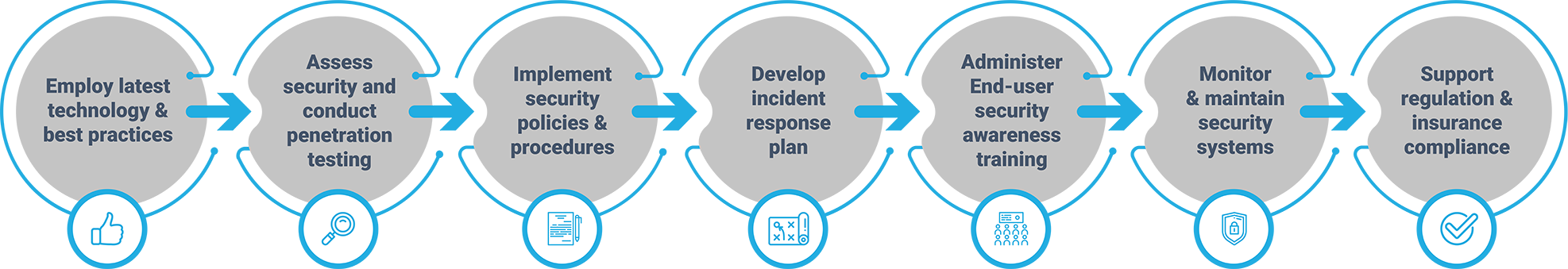
Protection Plans
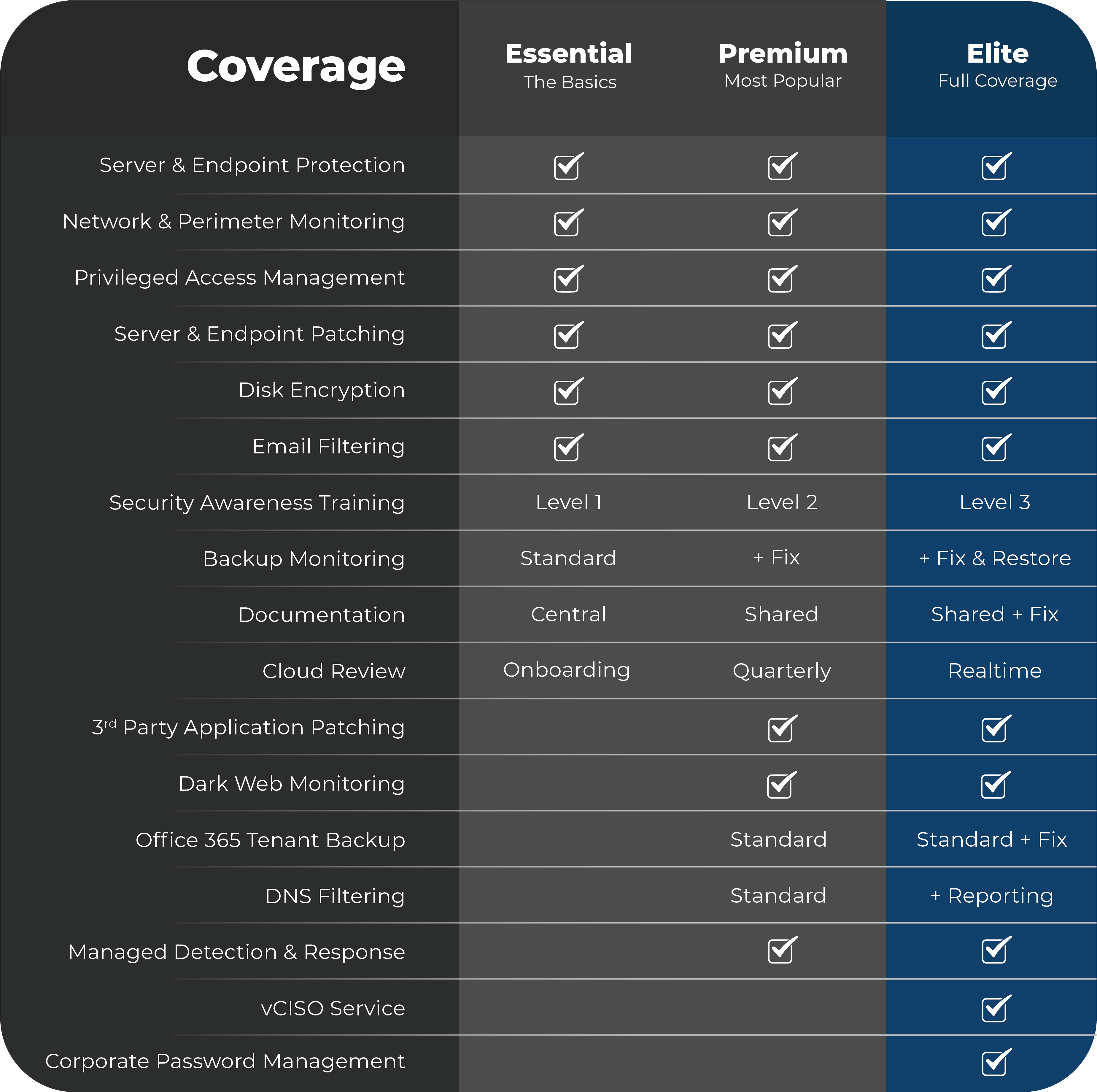
Get Your 100% Free, No Obligation Initial Consultation
Your pain? We understand. This is why we do what we do, and can provide you with an experience like no other.